WordPress is the most popular content management system (CMS) in the world. It powers over 40% of the websites on the internet. One of the key reasons for its popularity is the wide range of plugins available. These plugins add functionality to WordPress and help website owners customize their sites without needing to know how to code. However, these plugins can also be a security risk if not managed properly. In this article, we will explore WordPress plugin security and what you need to know to keep your website safe.
Introduction to WordPress Plugin Security
When it comes to WordPress plugin security, it’s essential to understand that vulnerabilities can exist both in the WordPress core and in third-party plugins. Plugins are created by developers who may not always prioritize security, and as such, it’s crucial to take the necessary precautions to prevent attacks.
Common Plugin Vulnerabilities
- Cross-Site Scripting (XSS) Attacks
- SQL Injection Attacks
- Remote Code Execution (RCE) Attacks
- Arbitrary File Upload Vulnerabilities
- Insecure Deserialization Vulnerabilities
We will discuss each of these vulnerabilities in detail and provide tips on how to prevent them.
Cross-Site Scripting (XSS) Attacks
XSS attacks occur when an attacker injects malicious code into a web page, which can then be executed by unsuspecting users. This vulnerability can occur when user input is not properly sanitized or validated by the plugin developer.
To prevent XSS attacks, plugin developers should always sanitize and validate user input. WordPress provides several built-in functions for this purpose, such as sanitize_text_field() and esc_html(). Plugin developers should also use nonces to prevent CSRF attacks.
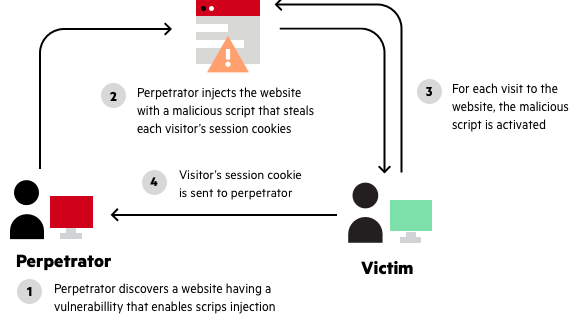
SQL Injection Attacks
SQL injection attacks occur when an attacker injects malicious SQL code into a web application’s database. This vulnerability can occur when user input is not properly sanitized or validated by the plugin developer.
To prevent SQL injection attacks, plugin developers should always use prepared statements and parameterized queries when interacting with the database. WordPress provides several built-in functions for this purpose, such as $wpdb->prepare().

Remote Code Execution (RCE) Attacks
RCE attacks occur when an attacker is able to execute arbitrary code on a target system. This vulnerability can occur when a plugin allows unauthenticated users to execute PHP code on the server.
To prevent RCE attacks, plugin developers should never allow unauthenticated users to execute PHP code. If a plugin requires server-side code execution, it should be properly authenticated and authorized.
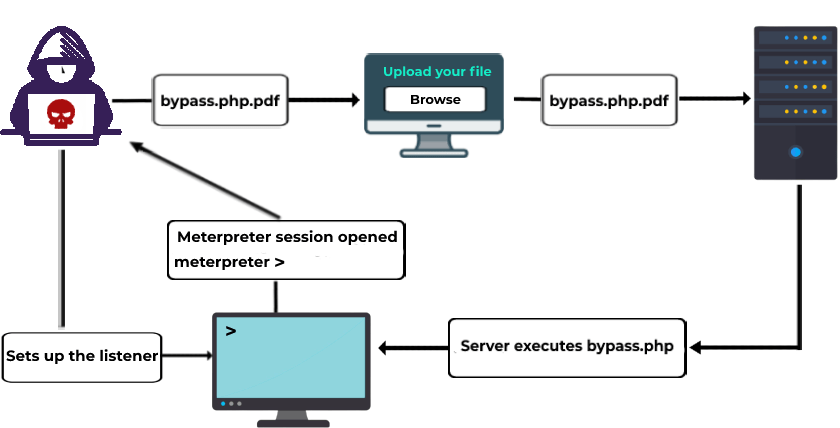
Arbitrary File Upload Vulnerabilities
Arbitrary file upload vulnerabilities occur when an attacker is able to upload and execute malicious files on a server. This vulnerability can occur when a plugin allows users to upload files without proper validation or sanitation.
To prevent arbitrary file upload vulnerabilities, plugin developers should always validate file types and enforce file size limits. Additionally, uploaded files should be stored outside of the web root directory to prevent direct execution.
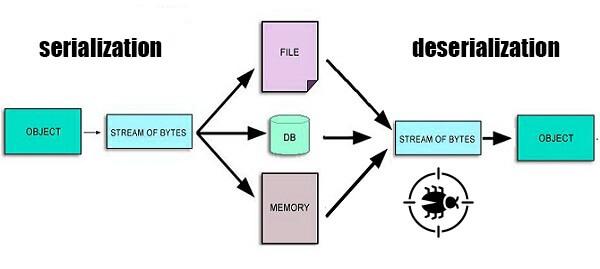
Insecure Deserialization Vulnerabilities
Insecure deserialization vulnerabilities occur when an attacker is able to modify serialized data in a way that allows them to execute arbitrary code on the server. This vulnerability can occur when a plugin does not properly validate or sanitize serialized data.
To prevent insecure deserialization vulnerabilities, plugin developers should never rely on serialized data from untrusted sources. Additionally, plugins should use a secure serialization format and validate input data before deserialization.
Best Practices for Plugin Security
In addition to understanding common plugin vulnerabilities, there are several best practices that plugin developers should follow to ensure their plugins are secure:
- Keep plugins up to date
- Use secure coding practices
- Use nonces to prevent CSRF attacks
- Sanitize and validate user input
- Use prepared statements and parameterized queries when interacting with the database
- Enforce proper file permissions
- Store uploaded files outside of the web root directory
- Use secure serialization formats
- Properly authenticate and authorize server-side code execution
- Use security plugins to scan for vulnerabilities

By following these best practices, plugin developers can greatly reduce the risk of their plugins being exploited by attackers.
Tips for Keeping Your Site Secure
While plugin developers have a responsibility to ensure their plugins are secure, website owners also have a role to play in keeping their sites safe. Here are some tips for keeping your site secure:
- Keep WordPress, plugins, and themes up to date
- Use strong passwords and two-factor authentication
- Install security plugins to scan for vulnerabilities and malware
- Use a reputable web host with strong security measures
- Regularly backup your site and store backups offsite
By following these tips, website owners can greatly reduce the risk of their site being compromised by attackers.
Conclusion
WordPress plugin security is an important aspect of website security that should not be overlooked. By understanding common plugin vulnerabilities and following best practices, plugin developers and website owners can greatly reduce the risk of their site being exploited by attackers. Always keep your WordPress site and its plugins up-to-date, use strong passwords and two-factor authentication, install security plugins, use a reputable web host, regularly backup your site, and store backups offsite.
Checkout more link : Top 10 Best WordPress Security Plugins to Keep Your Site Safe

